
Many businesses have been caught off guard by the pandemic, without any adequate security or continuity services in place for remote employees, scalable access to cloud/data centre applications, and a lack of network visibility or security on employee devices.
IT & Security leaders have quickly discovered that the “band-aid” remote access solutions– mostly legacy technology for fast fixes and something they have been flagging to the C-suite for some time– cannot provide what they now need for their company to be competitive and secure in the post-lock economy.
At the beginning of the outbreak of the pandemic, Marriott announced a data breach involving 5.2 million customers, and a cyber attack has forced Honda to shut down global operations. There have been several more reports of major companies being swept up in data breaches or cyber attacks. In addition, last month Interpol announced they had seen a sharp rise in attacks and expect it to get worse.
“There could be many companies with low levels of defence or centrally controlled structures, which make it more difficult to protect the increasingly mobile workers,” says Jason Parker-Smith, Aston Information Security. “In addition, due to a lack of awareness-raising training, many workers would be unknowingly vulnerable to threats such as phishing campaigns. For example, we can expect phishing attacks around a Covid-19 vaccine, so prepare colleagues now. ”
Now that lockdown constraints are starting to ebb and flow, CISOs are entering a ‘reassessing process’ of the crisis. Businesses should now be starting to take stock of, and change, their cyber security policies in light of Covid-19. Adapting IT and security measures to meet the demands of a new norm has to be a top priority. Businesses planning to migrate to a shared model or fully controlled security model in the near future are accelerating this post-lockdown move.
CISOs refocus on cyber security as cyber attacks increase
Opportunist criminals exploit coronavirus as part of their phishing attacks, malware, ransomware, and more. Hundreds of new COVID-19 themed phishing baits are produced every day according to PWC. They clarify, “We have identified criminal and state-sponsored campaigns exploiting COVID-19 and anticipate they will also use VPN and video conferencing software lures to take advantage of users unfamiliar with remote working.”
With the coronavirus epidemic generating new opportunities for cyber criminals, 70 % of companies see the importance of growing their investments in cyber security solutions.
According to McKinsey’s new report, which includes more than 250 global CISOs and security practitioners, crisis-driven security initiatives will remain the top budgetary priorities for the remainder of 2020. They expect CISOs to continue prioritising situations related to remote work and business continuity and then expect a period of hybrid operation where CISOs both take care of their immediate needs and begin to restore minimal support for longer-term or strategic cyber security demands.
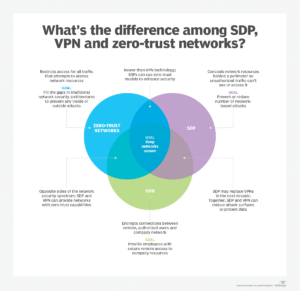
Technology and security features and capabilities that are vital to the organisation’s operations can vary widely and by industry. Anything from endpoint security, to bring-your-own-device, introducing software-defined permitters (SDP) and zero-trust networks, to VPN security to facilitate the division of labour between working at the office and work at home, need to be considered. Companies in regulated industries such as finance, for example, will need to prioritise compliance with the General Data Protection Regulation as they accelerate the transition of their business systems to the cloud.
Compliance with data protection obligations can mean that it is necessary for companies to have a separate data protection policy that sets out the duties of certain staff when handling personal data, including ensuring that it is stored safely at all times-even from home offices.
There is a lot to consider. Whatever the CISO roadmap is, it will certainly have to cover the maintenance of security operations, the mitigation of the risk of remote access to sensitive data and the introduction of MFA policies to allow employees to continue working remotely.
Is your remote working environment cyber secure?
Businesses may very well expect their security to be delivered “on a zero-touch basis, without physical meetings or equipment,” because IT departments need to be able to remotely set up, upgrade and enforce security solutions and managed services. Endpoints have now become a new battlefront, so protecting them is more critical than ever before.
Identity and access controls must be evaluated. We are seeing that businesses that have postponed the addition of MFA to legacy systems are accelerating their adoption or switching to cloud platforms. With more workers operating remotely, security teams managing business-critical networks are re-engineering who qualify for privileged access. For example, we believe that SMEs will invest in MFA services that integrate with collaborative tools and system-as-a-service platforms, including file sharing, remote desktop infrastructure and communication channels.
Remote access to email and other internal resources is another area of headache for security leaders. CISOs and their teams need to know how to assist, for example, help desk workers who may work in the office under ordinary circumstances and who might now face access problems that impact efficiency, such as problems with e-mail security tokens and remote desktop access.
Data security is at risk as well. Under pressure to meet financial constraints, CISOs are contemplating extending the length of time they use security applications prior to upgrade, especially for hardware-based applications (such as firewalls). This may mean that they give priority to paying for new functionality or patches for only the most important applications – a decision that in turn, could make companies more vulnerable to attacks.
Employees could be your biggest cyber security risk…and your greatest defence
The security training market will expand to meet demand. With cyber threats to remote employees growing, businesses are compelled to increase awareness training and to enlighten them about cyber hygiene.
According to Deloitte, employees are one of the most vulnerable cyber security “gaps.” “From our Cyber Intelligence Centre, we have observed a spike in phishing attacks, Malspams and ransomware attacks as attackers are using COVID-19 as bait to impersonate brands thereby misleading employees and customers. This will likely result in more infected personal computers and phones. Not only are businesses being targeted, end-users who download COVID-19 related applications are also being tricked into downloading ransomware disguised as legitimate applications.”
The cultural challenges raised by the disruption are also important. Away from the workplace, people have to interact differently, both in their jobs and with the organisation. IT access support is now being provided remotely, making cyber security knowledge even more relevant. It’s everyone’s obligation now.
Sure-up your supply chain during this pandemic crisis
A supply chain cyber attack, also identified as a third-party attack, occurs when a hacker invades an organisation’s system via a third-party vendor with access to their data. According to Gartner figures, 60 per cent of companies are now collaborating with more than 1,000 third parties and this figure is expected to rise even more over the next three years.
The time to ensure a cyber-resilient supply chain has never been more important. The Coronavirus pandemic is the greatest stress test for many supply chains, under tremendous strain to keep up with demand when attempting to keep up with ‘business as normal.’ Suppliers are more exposed than ever to disruption or data loss if vital processes are compromised, for example, and often hasty decisions disregard regulatory requirements in their hurry. Streamlining supplier security audits is important, as is understanding how deeply the supply chain network is traversed.
As we ride the wave of lockdowns and restrictions over the coming months and potentially years, CISOs have rightly focused on staying resilient despite operational and financial pressures. But now is the time to step back and evaluate, “What does the current reality look like in the coming months and years, and how do we plan for it?”
For more information on how we can help you navigate these unchartered waters, click here or get in touch for an initial consultation.




 Aston Information Security are Information Security consultants that specialise in assurance, audits, supply chain cyber security, data protection and risk management consultancy.
Aston Information Security are Information Security consultants that specialise in assurance, audits, supply chain cyber security, data protection and risk management consultancy.